Table of Contents
Introduction To DDoS Attack
Before diving into what is DDoS attack is, it’s essential to understand a basic Denial of Service (DoS) attack.
DoS attack is a cyberattack in which the attacker floods a website or server with more requests than it can handle, causing it to crash or become unavailable to legitimate users. The goal is to disrupt services and make them temporarily or permanently inaccessible.
Evolution to Distributed Denial of Service (DDoS)
A DDoS attack takes things to the next level. Instead of a single source attacking a system, a DDoS attack involves multiple devices sometimes thousands of devices working together to flood a target. These devices, often infected with malware and controlled by the attacker, make it much harder to stop the attack because it’s coming from many different locations.
As businesses and individuals rely more on digital services, DDoS attacks have become a serious and growing threat. From e-commerce sites to financial institutions, any service that relies on continuous uptime is a potential target. The cost of downtime can be substantial, and attackers know this, making it a favored method for causing damage or extorting money.
How DDoS Attacks Work
A typical DDoS attack begins when the attacker gains control of multiple devices through malware or other means. These compromised devices, often referred to as a botnet, are then used to send enormous amounts of traffic or requests to the target server. The goal is to overwhelm the target to the point where it can no longer function properly.
Let’s dive deeper into the anatomy of a DDoS attack and break it down step by step:
1. Botnet Formation
- The first stage of a DDoS attack involves an attacker gaining control over a large number of devices (such as computers, IoT devices, routers, etc.).
- This is often done through malware, phishing, or exploiting vulnerabilities in software, a simple example of this is by sending spam emails with any links or attachment
- The infected devices are called bots, these devices are unaware they are being used for malicious activities, as they silently follow the commands of the attacker.
2. Command & Control (C&C)
- The attacker maintains control over the botnet through a Command and Control server, which issues instructions to the compromised devices.
- This server tells the bots when, how, and where to launch the attack.
- The attacker often uses techniques to hide the C&C server to prevent being detected or stopped.
- Sometimes they use encryption or routing traffic through multiple layers (like the Tor network).
3. Attack Initiation
- Before starting an attack, The attacker selects a target, which could be a website, an online service, or a network infrastructure.
- The goal is to disrupt the normal operations of the target by overwhelming it with traffic.
- The bots in the botnet start sending an overwhelming number of requests or data packets to the target, flooding it with traffic.
4. DDoS as a service
- In some cases, botnets, which consist of networks of compromised devices, are made available for rent through “attack-for-hire” services.
- These services enable individuals with malicious intent, but little technical knowledge or experience, to effortlessly launch DDoS attacks.
- By paying a fee, even inexperienced attackers can gain access to a powerful network of bots and overwhelm a target, making DDoS attacks more accessible and widespread.
The Purpose of DDoS Attack
1. Disruption of Services
- The primary goal of many DDoS attacks is to disrupt the normal operations of a website, application, or network.
- By overwhelming the target with massive traffic, legitimate users are unable to access the service, leading to downtime.
- This can result in financial loss, damaged reputation, or loss of customer trust, especially for businesses that rely heavily on uptime and availability.
2. Financial Extortion
- Some attackers use DDoS attacks as a tool for extortion.
- They launch an initial attack and then demand a ransom (usually in cryptocurrency) to stop further attacks.
- This creates a financial burden on the target, who may either pay the ransom to restore service or invest in mitigation services to stop the attack.
- Paying the ransom can also encourage further attacks.
3. Competitive Advantage
- In some cases, attackers target business competitors to sabotage their online services. By causing their competitors’ websites or services to go offline, they gain an edge in the market, especially during critical sales periods or product launches.
- The targeted business may experience a loss of revenue and market share, while the attacker gains an advantage by maintaining operational continuity.
4. Hacktivism
- Hacktivists use DDoS attacks as a form of protest against governments, corporations, or organizations they disagree with.
- These attacks are often politically or ideologically motivated and aim to make a statement by taking the target offline.
- The attack disrupts the normal flow of communication, and access to information, or services provided by the targeted entity, bringing attention to the hacktivist’s cause.
5. Revenge or Personal Grudge
- DDoS attacks are sometimes carried out by individuals or groups seeking revenge for perceived wrongs, whether personal or professional.
- This could be a disgruntled employee, an unhappy customer, or someone who holds a personal vendetta against a business or individual.
- These attacks are usually targeted and may be short-lived, but they still cause disruption, leading to inconvenience and potential reputation damage for the target.
6. Cyber Warfare
- In the context of state-sponsored cyber warfare, DDoS attacks are used to destabilize or cripple a country’s infrastructure, such as government websites, financial institutions, or critical services like healthcare.
- The effects of cyber warfare-driven DDoS attacks can be devastating, leading to national security risks, loss of trust in the government or infrastructure, and widespread disruption to public services.
7. Testing Security Defenses
- Some attackers use DDoS attacks as a way to probe or test the security defenses of an organization.
- By launching a DDoS attack, they can observe how the target responds and use this information to plan more sophisticated attacks, such as data breaches or hacking attempts.
- This type of DDoS attack may not be intended to cause prolonged damage but serves as a way for the attacker to gather intelligence, making the target more vulnerable to future attacks.
8. Demonstrating Power or Capability
- Some cybercriminals launch DDoS attacks to show off their technical skills or the size of their botnet. This could be used to impress peers in hacker communities or to intimidate potential targets by showcasing their capacity to take down websites or services at will.
- The goal may not be long-term damage, but to gain recognition within a hacker network or use the attack as a warning to others.
Types of DDoS attacks
DDoS attacks can generally be categorized by which layer of the Open Systems Interconnection (OSI) model they target. The most common DDoS attacks occur at the Network (Layer 3), Transport (Layer 4), Presentation (Layer 6), and Application (Layer 7) layers.
By focusing on different aspects of a network or service, attackers aim to overwhelm specific parts of the infrastructure:
- Network Layer (Layer 3): Targets the data flow on the network.
- Transport Layer (Layer 4): Exploits protocols like TCP and UDP.
- Presentation Layer (Layer 6): Attacks encryption and encoding protocols.
- Application Layer (Layer 7): Mimics legitimate traffic to overwhelm specific applications.
Now, let’s dive into specific types of DDoS attacks:
- Application layer attacks
- Protocol attacks
- Volumetric attacks
1. Application layer attacks
An application layer attack happens when hackers use multiple computers or bots to repeatedly request the same resource from a server, eventually overwhelming it. For example, when you type a URL like https://hyscaler.com in your browser, an HTTP request is sent to the server. The server gathers all the necessary information for the page and sends it back to the browser. This process happens at the application layer.
In an attack, hackers abuse this by sending many requests, asking the server to keep fetching resources. These requests come from different IP addresses, making it hard for the server to detect the attack. The goal is to overwhelm the server until it crashes or slows down.
Types of Application Layer Attacks
- HTTP Flood Attacks: These involve sending many HTTP requests to a server using different IP addresses to overload the server. It’s like repeatedly refreshing a web page from many computers at the same time. The server eventually can’t handle all the requests, leading to a denial of service.
- Low-and-Slow Attacks: These attacks involve sending data very slowly or incompletely, which causes the server to keep the connection open longer than it should, using up its resources.
- GET/POST Floods: Hackers flood the server by sending too many GET or POST requests, which are used to load or submit information on a website, such as requesting web pages or submitting forms.
- Targeting Vulnerabilities: Some attacks focus on specific weaknesses in web servers, such as those in Apache, Windows, or OpenBSD. Hackers exploit these vulnerabilities to crash the server or make it unresponsive.
Example of Application Layer DDoS attack.
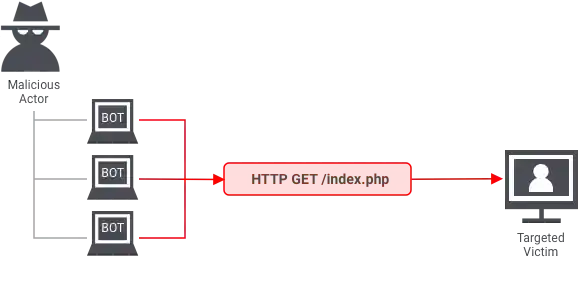
2. Protocol attacks
Protocol attacks aim to drain the resources of a server or its network equipment, like firewalls, routers, or load balancers. A classic example of a protocol attack is the SYN flood attack.
SYN Flood Attack Example
When two computers want to establish a secure connection, they begin with a TCP handshake, which involves three steps:
- The client sends a SYN packet (saying it wants to start a conversation).
- The server replies with a SYN-ACK packet (confirming it’s ready).
- The client then responds with an ACK to complete the handshake.
In a SYN flood attack, the attacker sends numerous SYN requests to the server, but these requests have fake (spoofed) IP addresses. The server responds to each request, waiting for the final ACK to complete the handshake. However, since the requests are fake, the server never receives the ACK and continues waiting, using up its resources to handle the half-open connections. As the server becomes overwhelmed with these requests, it can slow down or crash.
Example of Protocols DDoS attack.
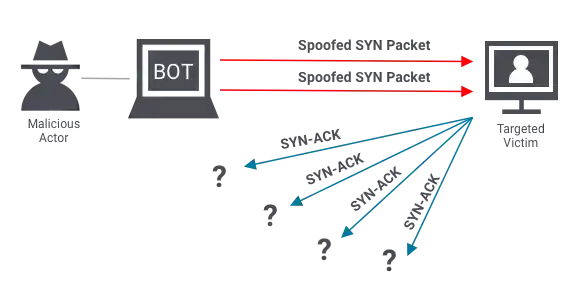
3. Volume-Based Attacks
These attacks aim to saturate the bandwidth of the target site, preventing legitimate traffic from reaching the server. Attackers often use amplification techniques or botnets to increase the data sent to the target. A botnet is a network of compromised devices that can be controlled remotely to send traffic to a target.
Common Types of Volume-Based Attacks
- UDP Floods: The attacker sends many UDP (User Datagram Protocol) packets to random ports on the target server. The server, trying to respond to each request, gets overwhelmed and can no longer handle legitimate traffic.
- ICMP Floods (Ping Floods): In this type of attack, the attacker sends a flood of ICMP (Internet Control Message Protocol) packets (ping requests) to the target. The target server gets bogged down responding to each ping, which consumes its bandwidth and resources.
- Spoofed-Packet Floods: The attacker sends huge amounts of fake data packets, using forged IP addresses to make it harder to block the malicious traffic.
Example of Volume-Based DDoS attack.
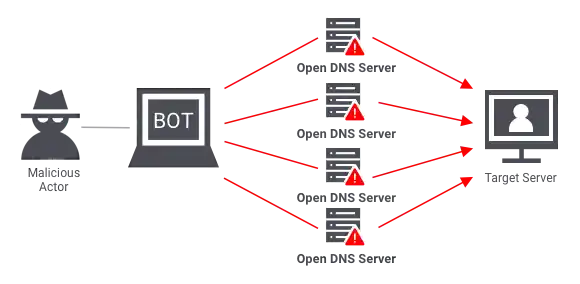
Signs Your System is Under DDoS Attack
Recognizing the early indicators of a DDoS attack can be the difference between a minor disruption and a major catastrophe. Being able to identify suspicious activity allows you to respond quickly and mitigate the damage.
While traffic spikes can sometimes be normal, these key indicators should raise alarm:
- Unusual Traffic Patterns: Sudden traffic spikes, especially during off-peak hours, or an unusual concentration of requests from specific geolocations or browsers, could signal a DDoS attack.
- Spike in Failed Login Attempts: An increase in unsuccessful login attempts may indicate a brute force attack aimed at overwhelming your servers. These could be part of a DDoS campaign, often disguised as credential stuffing.
- Frequent 5xx Error Codes: Look for increased occurrences of 500 or 503 error codes, which may suggest your servers are overwhelmed and unable to handle requests. Cross-check logs for abnormal patterns.
- External Users Reporting Downtime: A surge in complaints from users who can’t access your site, especially from different geographic locations, is a strong indication of a DDoS attack.
- Internal Software or Application Slowness: Employees experiencing slower or inaccessible internal applications could also be a sign. Their feedback during attacks is valuable for identifying ongoing issues.
Building a DDoS Attack Defense Strategy
Proactively preparing your defenses is key to minimizing the impact of a DDoS attack. While stopping an ongoing attack can be challenging, the right measures can help mitigate damage and protect legitimate users.
- Real-Time Packet Analysis: Implementing real-time traffic monitoring allows you to inspect every packet that enters your network. By setting predefined rules, you can quickly identify anomalies such as unusual traffic patterns or suspicious IP addresses. This helps in filtering out malicious traffic before it hits critical systems. Real-time packet analysis also enhances overall network visibility, enabling IT teams to react swiftly to threats and making it harder for attackers to launch stealthy attacks.
- Deploy a DDoS Defense System (DDS): A DDS is designed to detect and filter malicious traffic automatically. It can handle a variety of DDoS attack types, such as volumetric, protocol-based, and application-layer attacks. With real-time analysis, it distinguishes between legitimate and malicious traffic. The automation of DDS reduces the need for manual intervention, freeing up your IT resources to focus on other critical tasks. It also adapts to evolving threats, making it more effective against sophisticated attacks.
- Use a Web Application Firewall (WAF): WAFs are an essential layer of defense, particularly against application-layer (Layer 7) attacks, which are harder to detect. By filtering incoming HTTP/HTTPS requests based on specific rules, a WAF helps block malicious actors while ensuring legitimate traffic flows uninterrupted. A WAF is dynamic and can be updated with new rulesets on the fly, allowing it to respond quickly during an attack. It also protects against other common web threats such as SQL injection and cross-site scripting (XSS).
- Rate Limiting: By implementing rate limiting, you can control how many requests a server processes in a given time frame. This prevents servers from being overwhelmed by massive amounts of traffic during a DDoS attack. It ensures that legitimate users aren’t affected while keeping suspicious behavior in check. Rate limiting can also be tailored to specific users, IPs, or endpoints, allowing for more granular control over your traffic and further reducing the risk of server overload.
- Redundancy and Load Balancing: Redundancy and load balancing are critical components of a robust defense strategy. By distributing traffic across multiple servers, you avoid single points of failure. Even if one server becomes overwhelmed, the system redirects traffic to other available servers, maintaining service availability. Load balancing not only distributes incoming traffic but also improves overall system performance and scalability. Redundant systems also help in disaster recovery, ensuring that services remain available even if one server goes offline.
Conclusion: Are You Seriously Ready for a DDoS Attack?
DDoS attacks are increasingly common, more sophisticated, and capable of causing significant downtime, financial losses, and reputational damage. The 5 crucial gaps we’ve explored—preparedness, detection, mitigation, response, and recovery—highlight the importance of proactive measures and a comprehensive defense strategy.
Being ready for a DDoS attack requires more than just installing security tools. It’s about staying vigilant, monitoring traffic patterns, implementing layered security defenses, and having a solid incident response plan in place. Ensuring your systems are redundant, scalable, and capable of handling large surges in traffic is vital to minimize the damage of potential attacks.
By addressing these gaps and prioritizing cybersecurity as a long-term investment, businesses can strengthen their defenses, protect critical infrastructure, and ultimately ensure smoother recovery from any attack. The question isn’t if your organization will face a DDoS attack—it’s when. Taking action now will make all the difference when that moment comes.